
F95ADMIN Guide
Version 1.07
Fusion95 provides PC-to-UNIX connectivity via TCP/IP and RFC 1001/1002 NetBIOS. It enables a UNIX machine to be added to such a PC network as a File and Printer Server.
This guide explains how to use F95ADMIN to administrate your Fusion95 server from a Windows workstation.
F95ADMIN can be used to view, add, delete or modify the disk and printer resources which are shared by the Fusion95 server. This can be used to configure a server running in any security mode.
F95ADMIN can be used to view, add, delete or modify the users in the Fusion95 User Database of a Fusion95 server running in User-Level security mode.
When running in Share-level security, the ability to administrate the Fusion95 server from F95ADMIN is restricted by a password. When running in User-Level security, individual users in the Fusion95 User Database can be given administrator rights.
F95ADMIN includes a context sensitive on-line help to simplify the job of administering the Fusion95 server.
The following requirements must be met to use F95ADMIn to administrate a Fusion95 server.
The following information can be used to contact us for more information about our other products. It can also be used to obtain support help if your local distributor is unable to help you.
| Telephone: | +46 8 764 7040 |
| Fax: | +46 8 764 7044 |
| US tollfree: | 1-888-642-7745 |
The two e-mail addresses below can be used to contact Aprilís marketing and support departments. The web server contains up-to-date information about all our products and how to contact us. The ftp server contains the latest upgrades and support releases for our products.
| Web server: | http://www.april.se |
| ...or: | http://www.aprilsystem.com |
| Information: | april@april.se |
| Support: | support@april.se |
| Ftp server: | ftp://ftp.april.se |
This chapter describes how to install F95ADMIN onto a PC and how to uninstall it.
F95ADMIN can only be installed on a Windows 32-bit PC; running such versions as Windows 98 or NT 4. It cannot be installed on a Windows 16-bit PC; running versions such as Windows 3.11.
The following steps are used to install F95ADMIN from the release CD in a Windows PC:
The following describes how to uninstall F95ADMIN from your Windows PC:
When F95ADMIN is started it will search the network and find all the Fusion95 nodes. These it will display in a tree.
The tree can be expanded and Fusion95 nodes, Shared Disks, Shared Printers or users can be selected.
The following screen is an example of F95ADMIN. The Fusion95 node "UNIQUE" has been expanded and the Shared Disk resource "DEVELOPMENT" selected.
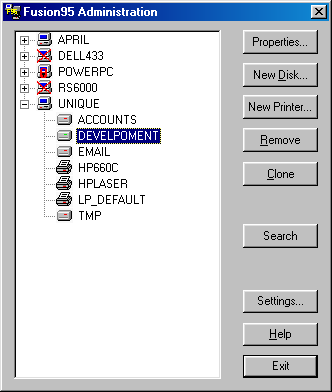
The buttons can be used to perform different functions on the selected item. Alternatively the item can be right-clicked using the mouse.
The following icons can appear in the F95ADMIN tree view:
| A Fusion95 node | |
| A Fusion95 node. This is a User-Level server to which the currently logged on user does not have administration rights. | |
| A Fusion95 node which does not support remote administration. It either has remote administration disabled or it is running a version of Fusion95 earlier than 4.0. | |
| A shared disk resource. | |
| A shared printer resource. | |
| User database (only on servers with User-Level security). |
Selecting the properties of a node shows information about that node. Information varies slightly depending on the type of node.
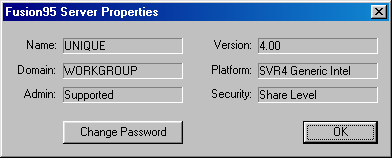
If the server is running Share-Level security, then the Change Password button can be used to set the serverís remote administration password.
When a shared disk resource is added, or has its properties changed, the following property sheet is displayed:
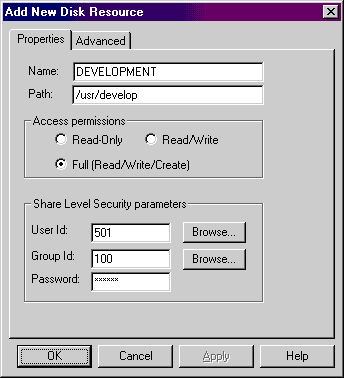
The name is that which identifies the shared device or path to the rest of the network. Any network machine requesting to USE the resource must specify this name. The resource short name must observe these format guidelines:
The path is the directory that you want to share. Precede the path name with a slash character (/). The name must be a valid UNIX directory (or sub-directory) name.
This option informs the server which access permissions the shared disk resource should have. This can be read-only access, read and write access, or read, write and create access.
This item only applies to Share-Level security, and will be ignored if User-Level security is enabled.
The User ID (UID) is a unique value distinguishing each user on the UNIX system. It can be entered in decimal, octal (with a leading 0), or hex (with a leading 0x or 0X).
This UNIX user will be specified as the owner of all files and directories created from a PC on this resource.
The default value is 0 which represents the UNIX system administrator (root).
The Browse button can be used to obtain a list of the users and their user id on the server.
When running on a Himalaya NonStop Server, you can either enter the Guardian NSK User ID or the OSS User ID. The other User ID will automatically be calculated and displayed. Entering an OSS User ID will also recalculate the Group ID.
This item only applies to Share-Level security, and will be ignored if User-Level security is enabled.:
The Group ID (GID) is a unique value distinguishing each group on the UNIX system. It can be entered in decimal, octal (with a leading 0), or hex (with a leading 0x or 0X).
This UNIX group will be specified as the owner of all files and directories created from a PC on this resource.
The default value is 0 which represents the UNIX system administrator (root).
The Browse button can be used to obtain a list of the groups and their group id on the server.
This item only applies to Share-Level security, and will be ignored if User-Level security is enabled .
The password to gain access to this resource. If you assign a password, this password must be provided by the requesting PC during the initial "USE" (redirection) request.
Passwords must not exceed 15 characters in length and may contain the following characters: A to Z, a to z, 0 to 9, underscore (_) and dollar ($).
When a shared disk resource is added, or has its properties changed, the property sheet contains an advanced dialog containing those properties that usually left at their default:
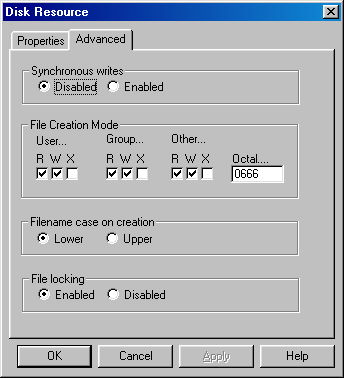
You can select whether or not you want synchronous writes enabled or disabled on this shared resource.
UNIX provides synchronous writes, allowing the user to bypass the buffer cache and write directly to disk. This greatly reduces the disk throughput, but guarantees that data is written immediately to disk. The server will not provide a write acknowledgment to the network until the write has been completed. UNIX system writes the disk cache to disk on a periodic basis, usually every 30 seconds.
The use of synchronous writes is appropriate for some applications, such as journal files, where it is important that the data be written to disk, but where the data will not be read back in the near future.
Using a UPS is preferred, rather than synchronous writes for more general applications due to the significant degradation in performance imposed by synchronous writes.
The file create mode for the shared resource. The file create mode is an octal number between 0 and 02777.
For example, to set the file creation mode to read/write/execute for the owner, and read-only for everyone else (rwxr--r--), the result of the addition would be 744.
Instead of typing the mode number, it is possible to change the file creation mode by clicking on the nine R W X bits.
When the group execution bit is not set, the 02000 bit is used to turn on UNIX mandatory locking.
Note: For record locking, you may change the file creation mode to allow mandatory record locking. Refer to the description of the chmod command in UNIX user documentation.
This entry identifies the alphabetic character case (upper or lower) that UNIX uses when creating file names for this shared resource. The recommended default is lower case.
MS-DOS and Windows for Workgroups ignore the character case of file names, but UNIX names are case-sensitive. This option informs the Fusion95 sever whether to use all upper or lower case when referring to files on this resource.
Windows 95, 98 and NT file names are case sensitive, but you cannot have two files with the "same" name but different case. This entry will specify the case of the filename when a file is created; this is especially useful when different workstations run a mixture of software only some of which supports mixed case filenames. If the pcserve.ini file does not have the smbprotocol parameter set to include NT_LM_012 then support will revert to using MS-DOS compatible filenames.
This option informs the server where it will perform file locking when a file on this shared resource is opened. File locking has no effect on record locking.
It is recommended that this option be enabled unless one of the two following apply.
When a shared printer resource is added, or has its properties changed, the following dialog box is displayed:
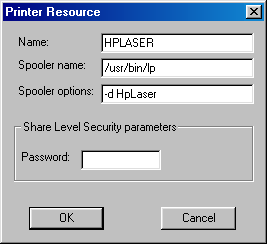
The name is that which identifies the shared printer to the rest of the network. Any network machine requesting to USE the resource must specify this name. The resource short name must observe these format guidelines:
The Spooler Name is the name of the UNIX spooler program, to be accessed through this shared printer resource. If no name is entered, the platform specific default UNIX spooler program for is used.
This are the command line options for the printer spooler, to be used when printing data from this printer resource. Any spaces entered on the options line will be removed.
A partial list of available options for the lp spooler command process are described in the following table:
| Option | Description |
|---|---|
| -d <name> | (Destination) This option allows you to specify the destination for the print output. This can be either the name of a printer or the name of a class. If no destination is specified, the default is used. For example: -dLASER01 |
| -c | (Copy) This option makes a copy of the file to avoid changes being made before the file is actually printed. |
-m |
(Mail) This option causes lp to notify the user by mail when the file is printed. MS-DOS users should use the UTERM program to log onto the UNIX system and retrieve the mail messages. |
| -w | (Write) This option is similar to the -m option, but a message is sent directly to your workstation or terminal using the write command after the file is printed. If the user is not logged on at the time, lp automatically uses the -m option, and sends mail instead. MS-DOS users running under multitasking environments can use UTERM to obtain immediate notification with the -w option. |
| -n <val> | (Number of copies=<val>) This option allows the user to specify the number of copies of the file they want printed. For example, to print 3 copies: -n3 |
| -o <option> | This option allows the user to specify an option (or string of options) to be passed to the print model. The option specified must be a valid option for the selected print model. View your selected model to determine available options. Two commonly used options are nobanner to suppress the printing of a job header page and land to print the output in landscape (as opposed to portrait) mode. |
Note: A complete list of lp options is included with the UNIX operating system documentation.
This item only applies to Share-Level security, and will be ignored if User-Level security is enabled . You are prompted to enter a password for the shared resource. If you do not want to assign a password, simply press Enter.
If you assign a password, this password must be provided by the requesting PC during the initial "USE" (redirection) request.
Passwords must not exceed 15 characters in length and may contain the following characters: A to Z, a to z, 0 to 9, underscore (_) and dollar ($).
The User Database exists only on servers with User-Level security. Expanding the User database icon shows a list of all users configured on the server.
This list shows two different types of users:
| Normal User | |
| User with administrator rights |
When a user is added, or has its properties changed, the following dialog box is displayed
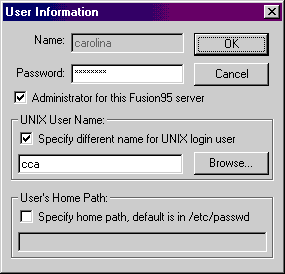
This is the PC users name. It should be the same name as you use when you start-up and login to the PC. It does not need to be the same name as used for the UNIX user's login, a different UNIX login user name can be associated with this use.
The user's password. This should be the same password as you use when you start-up and login to the PC. It does not need to be the same password as used for the UNIX user's login.
When checked, this allows the user to administrate this Fusion95 server from a Windows PC using F95ADMIN. This only enables administration for this specific Fusion95 server, not for all servers on the network. This does not make the user into a UNIX administrator, only a Fusion95 server administrator.
When enabled, the user icon will be changed to "carry a briefcase" in order to identify it as an administrator.
This allows you to specify a different UNIX login name for this user. If this user has the same name as the UNIX login then do not check the "specify different name" box. The Browse button can be used to obtain a list of the user names and their user id on the server.
The default Userís Home Path will be set to that configured in the UNIX system when the system administrator added the UNIX user. If this user has the same home path as the UNIX login then do not check the "specify different path" box. The UNIX home path is found in the /etc/passwd file.
Checking the "specify different path" box allows you to enter a different home path for this user than is normally used by the UNIX user. This will be used if automatic share of a home disk is enabled.
For details of how to automatically share a home disk, see the Fusion95 Userís Guide.
The Configuration Setting dialog is used to change the way the F95ADMIN program operates.
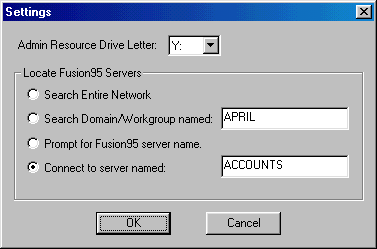
This drive letter is used by F95ADMIN to map the resource containing the Fusion95 server's configuration files. It should be set to drive letter not otherwise used on the Windows PC.
This is used to configure which method is used to locate the Fusion95 servers. Early versions of F95ADMIN did not have this capability and always searched the entire network neighborhood even if it stretched over many domains and even over WANs. Now the search can be limited to a specific Domain/Workgroup; this being useful in very large networks. Otherwise connection can be established with a specific Fusion95 server without searching; this being most useful in systems with only one, or very few, Fusion95 servers.