
User’s Guide
Version 5 and 6
Fusion95 provides PC-to-UNIX connectivity via TCP/IP and RFC 1001/1002 NetBIOS. It enables a UNIX machine to be added to such a PC network as a File and Printer Server, while allowing one or more windows in the PC to connect to the UNIX host and run UNIX applications.
The UNIX machine can act as a high-performance PC file server. Fusion95 implements SMB file and printer services including file and record locking on the UNIX system allowing thousands of DOS, Windows and OS/2 applications to reside on the UNIX file system.
The server supports enhanced SMB features such as long file names, share or user level security and 64KB data transfers.
The server is compatible with Microsoft’s Common Internet File Server (CIFS) standard.
UNIX applications can print to PC printers and PC users can print to all UNIX printers. Fusion95 allows all printers to be accessed by all users.
Fusion95 includes the high performance AniTa Windows terminal emulator. This supports many different terminal types (including ANSI, DEC VT220, VT320 and Wyse). AniTa is fully configurable, including keyboard and color customization. It provides access to Windows multimedia and programs from within a UNIX application.
Fusion95 supports a wide range of PC clients, including Windows95, Windows98, Windows 2000, Windows NT and XP. If you already have such an RFC-TCP/IP network, then a UNIX machine running Fusion95 can be added to your network without you needing to change any network software running on either workstations or servers. All existing users can immediately access UNIX applications and resources.
Installation is quick and easy, connecting UNIX to the LAN in less than 5 minutes. It is not necessary to reboot the UNIX machine.
Before installing Fusion95, ensure that the following components are present.
The following information can be used to contact us for more information about our other products. It can also be used to obtain support help if your local distributor is unable to help you.
The e-mail addresse below can be used to contact April’s marketing and support departments. The web server contains up-to-date information about all our products and how to contact us. The ftp server contains the latest upgrades and support releases for our products.
| Web server: | http://www.april.se |
| Ftp server: | ftp://ftp.april.se |
This chapter describes the installation of Fusion95 on a UNIX machine. If you are performing an upgrade of Fusion95 or already have POWERfusion on the UNIX machine, read the relevant sections at the end of this chapter before starting the installation.
There are three different methods of installing Fusion95.
Prior to installing Fusion95, the UNIX System and TCP/IP should be verified.
Fusion95 can run over any network interface card (NIC) for which TCP/IP is provided by UNIX including 10MB Ethernet and 100MB fast Ethernet. It uses the TCP/IP sockets interface.
TCP/IP and the NIC should be installed according to the documentation provided with UNIX. Verify that all required software and hardware is installed and operational; the netstat and ping commands can be used for this purpose.
Fusion95 uses sockets 137, 138 and 139. It should be verified that these are not in use by another program.
The netstat command can be used to show network status. It displays the contents of the various network related data structures in various formats, depending on the options selected. It can be used to check that TCP/IP is installed and running correctly. The -i option shows the interface state:
netstat -i
Run netstat without any option to show a list of active sockets:
netstat
Fusion95 uses sockets 137, 138 and 139. These are "well-known" sockets, defined in /etc/services. The following command can be used to determine that they are free:
netstat -n -a | grep 13[789]
The ping command is provided for TCP/IP to bounce packets between two nodes. It can be used to check that TCP/IP is installed and running correctly in both nodes.
Use the ping command to verify the TCP/IP network, specifying the name or IP address of a remote node, for example:
ping 192.0.0.10
Fusion95 requires that there is an entry in the /etc/hosts file for localhost. This is present in most TCP/IP implementations by default. For example:
127.0.0.1 loopback localhost
The following steps are used to install Fusion95 from the release CD in a Windows machine:
The following steps are used to install Fusion95 from the release CD in a UNIX machine:
Upgrade and evaluation versions of Fusion95 are available for download from the internet. These are provided in tar format. (Older versions were provided in compressed tar format "taz" and must first be converted to tar format using the uncompress command.) The following steps are used to install Fusion95 downloaded onto a UNIX machine:
Running the Fusion95 installation script is the final step of each of the three methods of installing Fusion95. The following describes the questions asked by the Fusion95 installation script. This script is: /tmp/usr/fusion95/install/install
You appear to have Fusion95 running, you should stop it before upgrading.
Do you want to stop Fusion95 now (y/n) ?
You appear to have an RFC NetBIOS installed and running. You cannot have more than one running in your UNIX machine. Fusion95 will not operate correctly unless you remove it.
Do you want to continue (y/n) ?
Note: some platform specific implementations of Fusion95 will recognize a conflicting NetBIOS and allow you to automatically remove it before continuing.
The fusion node name is currently set to: FUSION
Is this OK (y/n) ?
If this is not OK, a different name can be selected:
Please enter the network name (8 characters or less):
The workgroup/domain name is currently set to: WORKGROUP
Is this OK (y/n) ?
If this is not OK, a different name can be selected:
Please enter the workgroup/domain name (15 characters or less):
If this is a first-time or trial installation, you may not have a Fusion95 authorization code. Without an authorization code you will be able to test Fusion95 for 30 days.
Please find your authorization code.
If you do not have an authorization code, you may still evaluate Fusion95 for 30 days.
Do you have a Fusion95 authorization code (y/n) ?
If Y was entered, you will be asked to enter the code:
The license code consists of 16 characters. It may be entered as a 16 character string or in blocks of 4 separated by dashes ‘-’.
Enter the new license code (type q to quit):
The system will now be copied to /usr/fusion95.
/usr/fusion95/f95start
The installation then prompts to see if it should execute this command for you, in order to start Fusion95 immediately.
Do you want to start Fusion95 now (y/n) ?
Type Y to start Fusion95 immediately.
Before installing an upgrade, stop the existing Fusion95 system using the command:
/usr/fusion95/f95stop
It is possible to install a new version of Fusion95 directly over an older version without first removing the previous version. Existing configuration files (such as shared disk and printer resources) will be retained.
The normal installation procedure should be used as described previously in the chapter. Note that the answers given to the previous installation will now be the defaults for the installation of the upgrade.
It is possible to install Fusion95 onto a system that already has POWERfusion installed. The normal installation procedure should be used.
POWERfusion and Fusion95 reside in different locations on the UNIX system and do not share configuration files. It is thus possible to run both simultaneously.
Upon completion of a demonstration or evaluation, the applied Fusion95 software may be removed using the following procedures.
The following list contains the major steps involved in removing Fusion95 from a UNIX computer. Each step is described in detail elsewhere in this document.
In order to stop Fusion95, the f95stop script should be executed. Enter the command:
/usr/fusion95/f95stop
It is recommended that the Fusion95 configuration information be saved for later reference. This is best done by performing an UNIX backup of the /usr/fusion95 catalog.
In order to remove Fusion95, the remove script should be executed. The program should not be executed while the user is in the /usr/fusion95 catalog or tree.
Enter the command:
/usr/fusion95/install/remove
The file and print server in Fusion95 makes UNIX disk and printer queue resources available to PC network workstations. It uses the SMB and CIFS protocols over TCP/IP. This chapter provides detailed instructions on configuring the server.
During Fusion95’s initial installation, a default configuration containing one shared disk and one shared printer with share-level security will be created. This server will work straight away without requiring any configuration.
After completing the installation, it might be necessary to change the security mode.
It is usual to modify these default shares, and add additional shared resources; this is done from a UNIX terminal or a Windows PC.
Once the configuration is finished, new shared resources will be immediately available to the PCs on the network. Any shared resource that was removed, is still available to any PC workstation that was using the resource prior to its removal, but no new PC workstation can access the resource.
There are three different types of security available to Fusion95. These are Share-Level, User-Level and Unix-Level security.
Share-Level security is the easiest to use and administrate, and it is this we recommend you use unless you really need functionality from one of the others.
Whether Share-Level, User-Level or Unix-Level security is used is determined by the secmode= parameter in the pcserve.ini file.
Share-Level security has shared resource access determined when the resource is used by validating the resource password. An example of this is a Windows 95 server.
User-Level and Unix-Level security have shared resource access determined at logon, time by validating the user id and password. An example of this is a Windows NT server.
The security type is always configured on a per-server basis. It is not possible to have different type of security for different shared disks.
Share-Level works the same for both core and extended SMB protocols. Access to disks is determined at resource connection time. Disk access is controlled by the specification of passwords.
Users will have full access to all files on the shared resource. The UNIX user id and access permission of any files created will be determined on a shared resource basis.
Correct use of User-Level security requires that an extended SMB protocol is negotiated by the client (i.e. anything but the core protocol: PC_NETWORK_10). This allows the client to send a session set-up request to the server containing the user-name and password. These will be validated against Fusion95’s User Database before access is allowed. Once access is permitted, the user can NET USE all shared resources without specifying a password, and obtain access rights according to the UNIX user account.
If a core protocol client attempts to gain access to a User-Level server, special rules apply. A session setup will be dynamically performed for the client when it first attempt to connect to a shared resource. In this case the name of the client’s workstation will be used as the user-name and the password specified for the resource connection will be used as the user's password.
If the user-name and password cannot be validated, then access to the server will normally be denied. It is however possible to allow guests to access the server; users without a valid account on the server will be logged on as a guest. In order to do this the guest= parameter must be included in the pcserve.ini file to specify the user-names whose access rights the guest will be given. The default is NOT to permit guests access.
To simplify the use of Fusion95 in User-Level security, a special configuration utility has been provided. Run:
/usr/fusion95/install/ulevel
This script will enable User-Level security. It will also allow you to create the Fusion95 User Database based on the contents of the UNIX system’s /etc/passwd file.
Unix-Level security is provided for backwards compatibility with Fusion95 version 3. User names and passwords will be validated against the UNIX security databases (e.g. /etc/passwd and /etc/shadow) before access is allowed. Once access is permitted, the user can NET USE all shared resources without specifying a password, and obtain access rights according to the UNIX user account.
Core protocol restrictions and guest user access are the same as for User-Level security.
Note: The password encryption used by Microsoft Windows is different from that used by UNIX in the /etc/passwd and /etc/shadow files. Therefore Unix-Level security requires that the support for Microsoft Windows password encryption is disabled (using pwcrypt=0 in the pcserve.ini file).
There are two methods available for sharing a disk resource. This can be performed either from a UNIX terminal session using pcconfig or from a Windows PC using F95ADMIN. This user’s guide covers configuration from UNIX, the F95ADMIN program is documented separately.
Once the configuration is finished, new shared disks will be immediately available to the PCs on the network. Any shared resource that was removed, is still available to any PC workstation that was using the resource prior to its removal, but no new PC workstation can access the resource.
To configure shared disk resources, run the following command:
/usr/fusion95/pcconfig
and select "File Server Parameters". This will allow you perform one of the following functions on a shared disk resource:
The resource short name is a name that identifies the shared device or path to the rest of the network. Any network machine requesting to USE the resource must specify this name. The resource short name must observe these format guidelines:
This item only applies to Share-Level security, and will be ignored if User-Level security is enabled.:
The user ID (UID) is a value established for each user on the UNIX system. It can be entered in decimal, octal (with a leading 0), or hex (with a leading 0x or 0X). Alternatively, a user login may be entered.
At create time, if a valid user login is entered, the user ID, group ID, and path fields are filled-in automatically and reflect the numeric UID and GID values as well as the home path for that user. If a numeric UID is entered, pcconfig prompts for a group ID (GID), and then prompts for the path.
Note that the easiest method for SHARING a resource is to enter a valid login name for this value and allow pcconfig to fill the UID and GID fields.
This item only applies to SHARE-LEVEL security, and will be ignored if USER-LEVEL security is enabled. This item only applies to SHARE-LEVEL security, and will be ignored if USER-LEVEL security is enabled. This item only applies to SHARE-LEVEL security, and will be ignored if USER-LEVEL security is enabled.
You are prompted to enter the path name of the resource you want to share. Precede the path name with a slash character (/). The name must be a valid UNIX directory (or sub-directory) name. You may enter a valid user id to obtain that user’s home directory.
If you entered the user login name as the user ID in the previous step, the path name of the user's home directory is automatically entered.
This item only applies to Share-Level security, and will be ignored if User-Level security is enabled . You are prompted to enter a password for the shared resource. If you do not want to assign a password, simply press Enter.
If you assign a password, this password must be provided by the requesting PC during the initial "USE" (redirection) request.
Passwords must not exceed 15 characters in length and may contain the following characters: A to Z, a to z, 0 to 9, underscore (_) and dollar ($).
You are prompted to select whether or not you want synchronous writes performed on the selected shared resource. Simply press Enter, to get the recommended value; no.
UNIX provides synchronous writes, allowing the user to bypass the buffer cache and write directly to disk. This greatly reduces the disk throughput, but guarantees that data is written immediately to disk. The Fusion95 server will not provide a write acknowledgment to the network until the write has been completed. UNIX system writes the disk cache to disk on a periodic basis, usually every 30 seconds.
The use of synchronous writes is appropriate for some applications, such as journal files, where it is important that the data be written to disk, but where the data will not be read back in the near future.
Using a UPS is preferred, rather than synchronous writes for more general applications due to the significant degradation in performance imposed by synchronous writes.
You are prompted to enter the file create mode for the shared resource. The file create mode is an octal number between 0 and 02777. Simply press Enter, to get the recommended value; 0666 (rw-rw-rw-).
For example, to set the file creation mode to read/write/execute for the owner, and read-only for everyone else (rwxr--r--), the result of the addition would be 744.
When the group execution bit is not set, the 02000 bit is used to turn on UNIX mandatory locking.
Note: For record locking, you may change the file creation mode to allow mandatory record locking. Refer to the description of the chmod command in UNIX user documentation.
This entry identifies the alphabetic character case (upper or lower) that UNIX uses when creating file names for this shared resource. Simply press Enter, to get the recommended value; lower case (L).
MS-DOS and Windows for Workgroups ignore the character case of file names, but UNIX names are case-sensitive. This option informs the Fusion95 sever whether to use all upper or lower case when referring to files on this resource. The UNIX default for file names is lower case.
Windows 95, 98 and NT file names are case sensitive, but you cannot have two files with the "same" name but different case. This entry will specify the case of the filename when a file is created; this is especially useful when different workstations run a mixture of software only some of which supports mixed case filenames. If the pcserve.ini file does not have the smbprotocol parameter set to include NT_LM_012 then Windows95 and NT workstations will revert to using MS-DOS compatible filenames.
If you want your UNIX and MS-DOS files to be readily distinguishable under UNIX, select U (or u). This selection allows UNIX files, which typically have lower-case names, to be invisible to MS-DOS.
Alternatively, if you want to frequently use files from both operating systems interchangeably, then select L (or l). This procedure allows convenient movement of data between systems but, makes it difficult to distinguish files created under different operating systems on a directory listing.
This option informs the server where it will perform file locking when a file on this shared resource is opened. File locking has no effect on record locking. Simply press Enter, to get the recommended value; yes.
It is recommended that this option be set to yes (Y) unless one of the two following apply.
This option informs the server which access permissions the shared disk resource should have. Type 'R' for read-only access, 'RW' for read and write access, and 'RWC' for read, write and create access. Simply press Enter, to get the recommended value; full (RWC).
There are two methods available for sharing a printer resource. This can be performed either from a UNIX terminal session using pcconfig or from a Windows PC using F95ADMIN. This user’s guide covers configuration from UNIX, the F95ADMIN program is documented separately.
Once the configuration is finished, new shared printers will be immediately available to the PCs on the network. Any shared resource that was removed, is still available to any PC workstation that was using the resource prior to its removal, but no new PC workstation can access the resource.
To configure shared printer resources, run the following command:
/usr/fusion95/pcconfig
and select "Printer Server Parameters". This will allow you perform one of the following functions on a shared printer resource:
The resource short name is a name that identifies the shared printer to the rest of the network. Any network machine requesting to USE the resource must specify this name. The resource short name must observe these format guidelines:
This item only applies to Share-Level security, and will be ignored if User-Level security is enabled . You are prompted to enter a password for the shared resource. If you do not want to assign a password, simply press Enter.
If you assign a password, this password must be provided by the requesting PC during the initial "USE" (redirection) request.
Passwords must not exceed 15 characters in length and may contain the following characters: A to Z, a to z, 0 to 9, underscore (_) and dollar ($).
The Spooler Name is the name of the UNIX spooler program, to be accessed through this shared printer resource. If no name is entered, the platform specific default UNIX spooler program for is used.
You are prompted to enter options for the printer spooler, to be used when printing data from this printer resource. Any spaces entered on the options line will be removed.
If you do not want to add any options, simply press Enter to obtain a null value.
A partial list of available options for the lp spooler command process are described in the following table:
| Option | Description |
|---|---|
| -d <name> | (Destination) This option allows you to specify the destination for the print output. This can be either the name of a printer or the name of a class. If no destination is specified, the default is used. For example: -dLASER01 |
| -c | (Copy) This option makes a copy of the file to avoid changes being made before the file is actually printed. |
-m |
(Mail) This option causes lp to notify the user by mail when the file is printed. MS-DOS users should use the UTERM program to log onto the UNIX system and retrieve the mail messages. |
| -w | (Write) This option is similar to the -m option, but a message is sent directly to your workstation or terminal using the write command after the file is printed. If the user is not logged on at the time, lp automatically uses the -m option, and sends mail instead. MS-DOS users running under multitasking environments can use UTERM to obtain immediate notification with the -w option. |
| -n <val> | (Number of copies=<val>) This option allows the user to specify the number of copies of the file they want printed. For example, to print 3 copies: -n3 |
| -o <option> | This option allows the user to specify an option (or string of options) to be passed to the print model. The option specified must be a valid option for the selected print model. View your selected model to determine available options. Two commonly used options are nobanner to suppress the printing of a job header page and land to print the output in landscape (as opposed to portrait) mode. |
Note: A complete list of lp options is included with the UNIX operating system documentation.
There are two methods available for User Database administration. This can be performed either from a UNIX terminal session using pcconfig or from a Windows PC using F95ADMIN. This user’s guide covers configuration from UNIX, the F95ADMIN program is documented separately.
Once the configuration is finished, new users will be immediately available to the PCs on the network. Any user that was removed, is still available to any PC workstation that was using it prior to its removal, but no new PC workstation can gain access to resources via that user.
To configure users, run the following command:
/usr/fusion95/pcconfig
and select "User Parameters". This will allow you perform one of the following functions on a shared printer resource:
This should be the same name as you use when you start-up and login to the PC. It does not need to be the same name as used for the UNIX user's login, a different UNIX login user name can be associated with this use.
The user's password. This should be the same password as you use when you start-up and login to the PC. It does not need to be the same password as used for the UNIX user's login.
This allows the user to administrate this Fusion95 server from a Windows PC using F95ADMIN. This only enables administration for this specific Fusion95 server, not for all servers on the network. This does not make the user into a UNIX administrator, only a Fusion95 server administrator.
This allows you to specify a different UNIX login name for this user. If this user has the same name as the UNIX login then leave this empty.
This allows you to specify a different home path for this user than is normally used by the UNIX user. The UNIX home path is found in the /etc/passwd file. If this user has the same home path as the UNIX login then leave this empty. This will be used if automatic share of a home disk is enabled.
This section provides instructions for configuring the server’s parameters. Changes to the server’s configuration parameters require that the server be restarted in order to take effect.
Three parameters can be configured via the pcconfig program, the remaining parameters are contained in the pcserve.ini file.
The following parameters are configured using the pcconfig program. To change them run the following command:
/usr/fusion95/pcconfig
This number represents the average number of open files
that each client PC can have on the server. A File Identification (FID) Table will be created by the server with the number of entries equal to the product of the FID Table Size and the number of authorized users.
The default FID table size is 50. Enter the desired value (or * to use the default).
This table resides in shared memory; make sure the UNIX machine has sufficient shared memory configured to accommodate this table.
The DIR table size configuration option specifies the number of directory search table entries created by each of the server’s child tasks. It is used when the client PC requests nested searches through directories. This table is specific to each Fusion95 server process.
This value should be set greater than the total number of directories beneath the highest level shared directory.
The default DIR table size is 120, and the maximum is 256. Enter the desired value (or * to use the default).
The path name of the directory in which the spool files will be created and the case of the file names can be configured.
Path
You are prompted to enter the path of the directory used to hold spool files. Precede the path name with a slash character (/). The name must be a valid UNIX directory (or sub-directory) name.
Case
This entry identifies the alphabetic character case (upper or lower) that UNIX uses when creating spool file names.
MS-DOS ignores the character case of file names, but UNIX names are case-sensitive. This option informs the sever whether to use all upper or lower case when referring to files on this resource. The UNIX default for file names is lower case.
The following parameters are configured by editng the pcserve.ini file. To change them run the following command:
/usr/fusion95/cfg/pcserve.ini
Further information about the available configuration parameters in the pcserve.ini file is available in the inifile.txt file which is copied into /usr/fusion95/cfg at install time.
Format:
secmode=<number>
This value tells the server whether to use Share-Level, User-Level or Unix-Level security. These are explained in the "Security Modes" section earlier in this chapter.
Share-Level 0
Unix-Level 1
User-Level 3
The default is Share-Level security:
secmode=0
Format:
pwcrypt=<number>
This enables or disables support for Microsoft Windows password encryption.
Enabled 1
Disabled 0
This option must be disabled in order to support Unix-Level security which uses a different encryption method in the /etc/passwd and /etc/shadow files.
The default is password encryption enabled:
pwcrypt=1
This should normally be enabled in order to support Windows98 and later versions of NT 4 and Windows95. If this is disabled in Fusion95 then plain text passwords must also enabled in the Registry of PCs running these Windows versions .
Enable Plain Text Passwords
CAUTION: Make sure you know how to run the registry editor correctly. Using it incorrectly can cause serious problems.
On Windows NT:
On Windows 95 and Windows 98:
Format:
guest=<string>
This string tells the server the name of the user to use as guest when performing session setup. A null string will cause the server to deny access as guest. This option will be ignored when Share-Level security is configured.
For example:
guest=keith
The default denies guest access:
guest=
Format:
homeshare=<resource_name_string>
homemode=<access_mode_number>
homeminuid=<number>
homemaxuid=<number>
homecase=<number>
When using User-Level or Unix-Level security it is possible to make the server automatically share the home directories of users. This make configuration of the server shared resources much easier.
Use the homeshare option to enable this feature and to specify the name of the shared resource. This is used when connecting to the shared resource. If you specify "homeshare=HOME$" then use the following command line to access it:
NET USE H: \\FUSION95\HOME$
If you want to restrict the range of users who have shared disks then set the homeminuid and homemaxuid to the minimum and maximum user ids that are allowed access to their home disks.
In order to specify which mode is used when creating files on this shared disk use the homemode option.
In order to specify which case is used for this shared disk, set the homecase option to 1 (lower - default) or 0 (upper).
For example:
homeshare=HOME
homemode=0755
homeminuid=400
homemaxuid=500
homecase=1
The defaults do not automatically share the users home directory:
homeshare=
homemode=0750
homeminuid=0
homemaxuid=32767
homecase=1
Format:
smbprotocol=<number>
This option tells the server which protocols it can negotiate. It will start at the highest number and work downwards trying to find an acceptable protocol. The server will always negotiate the original PC NETWORK 1.0 protocol as a last resort.
This value should be set by adding together the following bit values.
NT_LM_012 32
MICROSOFT_NETWORKS_30 2
LANMAN_10 1
PC_NETWORK_10 0
For example:
smbprotocol=0
The default will negotiate all four protocols:
smbprotocol=35
Note: The NT_LM_012 protocol is required for Windows 95, Windows98 and NT in order for the advanced features of these platforms (such as long filename support) to work correctly.
Format:
bigbuffers=<number>
This option tells the server whether to assign 64KB buffers for use in the read raw and write raw commands. It can be set to one of the following values:
NEITHER 0
READ RAW 1
WRITE RAW 2
BOTH 3
The default value permits the client to use big buffers for both reading and writing:
bigbuffers=3
Note: The use of big buffers requires that an extended SMB protocol is negotiated (LANMAN_10 or greater). If core SMB protocol (PC_NETWORK_10) is negotiated, this option has no effect.
Note: If the NT_LM_012 protocol is negotiated then any value other than bigbuffers=0 implies both read and write. It is not possible with this protocol to use big buffers for either just read or just write.
Format:
buffersize=<number>
This parameter determines the size of the data buffer used by the server. The buffer size determine the total amount of data sent on the network including the SMB header.
For example:
buffersize=4144
Setting this value to 0, causes the server to use its default buffer size (currently 16384).
Format:
maxdisksize=<number>
This parameter can be used to specify the maximum disk size returned by the server. It specifies a value in kilobytes. If set, the server will never report a disk size or disk free space larger than this value. The default is no maximum disk size.
This value should be used to solve a problem with some old DOS programs which do not accept disk space greater than 1GB. They often complain of "not enough free disk space" if the free disk space exceeds 1GB.
For example:
maxdisksize=1048576
Format:
logging=<number>
This value tells the server what information to write to the log file. This value should be set by adding together the following bit values.
SESSION CONNECTS 1
SESSION DISCONNECTS 2
ABORTS 4
PROTOCOL 8
LOGINS 16
TREE CONNECTS 32
LOG-OFFS 64
ERRORS 128
SHOW EVEN PASSWORDS 256
SHOW EVEN IPC TCONS 512
The default is
logging=7
Example:
logging=87
A value of 87 (i.e. 1+2+4+16+64) will cause the following events to be logged:
1. SESSION CONNECTS
2. SESSION DISCONNECTS
4. ABORTS
16. LOGINS
64. LOG-OFFS.
Format:
errlog=<number>
The logging=128 option will log all errors returned EXCEPT "file not found". Set errlog=2 in the pcserve.ini file if DOS Error 2 "file not found" should also be logged.
Format:
internalcharset=<number>
This option specifies the character set to use internally on the UNIX disk. It can be set to one of the following values:
IBM PC 0
ISO 8859 1
WRITE RAW 2
The default is
internalcharset=0
Format:
triggers=<number>
This option is used to enable or disable triggers. Triggers are explained in Appendex B. This can have one of the following values:
Disabled 0
Enabled 1
Enabled with trace 2
The default with triggers disabled is:
triggers=0
Format:
checkbrowseaccess=<number>
This option controls which shared disk and printer resources are listed when browsing. When set to zero, all resources are listed. When set to one, only those resources to which the user has access are listed.
The default is to only list those resources to which the user has access:
checkbrowseaccess=1
Format:
dontbrowsenetlogon=<number>
This option controls whether the NETLOGON shared disk is listed when browsing. When set to one, this resource is not listed.
The default is to list the NETLOGON disk when browsing:
dontbrowsenetlogon=0
With Fusion95 installed in a network, the following four methods of network printer usage are available:
This chapter explains how to configure and use a printer client so that a UNIX user can print on any PC printer in the network.
The File and Print Server chapter explains how to configure and use a printer server so that a PC user can print on any UNIX printer.
In order to use a PC printer from a UNIX machine, you need to configure a Printer Client in the UNIX machine.
A program called smbprtup is used to implement an SMB printer client. Data directed to this program’s standard input will be sent to an SMB printer server somewhere on the network.
Configuration files reside in the /usr/fusion95/cfg catalog and are named lprt00 to lprt999. They specify the name and location of the SMB printer server, access permissions, as well as any translation of LF to CR/LF and national characters.
To configure the printer client, run the smbprt.sh program and select which printer to configure.
/usr/fusion95/smbprt.sh
This program can also be started by running the menu shell and selecting:
Printer Client => Printer Configuration
The following describes each of the configuration options:
This is the name of the remote server to which the printer is attached.
Fusion95 will use broadcasts to obtain the IP address of this node. If Fusion95 and the printer server do not reside on the same broadcast network, then Fusion95 will not find the printer server. It will then search the DNS and/or the /etc/hosts file to attempt to find a matching name, even checking for all upper or all lower case.
This is the name of the printer. Together with the server name, it identifies the destination printer resource.
This is the password required to gain access to the printer resource. If the printer is not password protected, a value of asterisk (*) should be entered.
This is a user name required to gain access to the printer resource. If the printer is connected to a server with share-level security then a value of asterisk (*) should be entered as no username is required. If the printer is connected to a server with user-level security then a user name should be entered. This username together with the previous entered password should be sufficient to access the printer. If no username is specified, the Fusion95 server's name will be used.
This is normally set to yes. It should be set to no if the printer is on a node outside of the current broadcast network. In this case Fusion95 will not attempt to broadcast to locate the printer but instead go directly to the DNS and/or the /etc/hosts file. This will remove an overhead of 10 seconds.
If enabled, this feature will add a CR before each LF sent to the printer. It should only be used when sending text output to the printer. This is of special use when printing to HP laserjet printers.
This option allows character set translation, if the character set in UNIX is different from that in the printer. It should only be used when sending text output to the printer.
The following example configures lprt03, to use a printer called HPLASER> on the server SERVER1.
Access rights to the printer will be determined by the username KEITH and no password.
The insertion of CR prior to a LF is turned on (a requirement of the HP laser), but no national character translation is performed.
SMB printer client configuration
================================
Which printer config file do you want to setup (0-999): 03
Configuration options for SMB printer client '/usr/fusion95/cfg/lprt03.cfg'
1. Show printer set up
2. Set up printer
3. Remove printer set up
4. Print a test page
5. Choose a different printer client
x. Exit
--> 2
Enter the print server/spooler name: SERVER1
Searching Network for Server: SERVER1 ...please wait... OK
Printer name on node SERVER1: HPLASER
Password or * for no password : *
Username or * for no username : KEITH
If then printer is connected to the local network, then
broadcasts will be used to find its IP address. Otherwise
the /etc/hosts file and any DNS will be used.
Is the printer connected to this local LAN yes or no : yes
Should insertion of CR before a LF be turned on or off: on
Should character translation be turned on or off: off
There are 3 different methods for printing on a PC printer from UNIX. These are:
The start of Fusion95 will automatically set-up eight named pipes named /dev/lprt00 through /dev/lprt07. These will direct print output via the smbprtup printer client program to their respective network printers.
The configuration files /usr/fusion95/cfg/lprt*.cfg will be used for the respective named pipes. This provides a very easy way of directing print data from any application to a named pipe looking exactly as a serial device from the application.
It is very easy to expand the number of named pipes to the maximum of 1000 by modifying the named pipe startup section in the Fusion95 startup script /usr/fusion95/f95start.
Named pipe printing can be tested using the following UNIX command:
ls -l > /dev/lprt03
If the output for some reason fails, the last error message is logged in /usr/fusion95/lprt*.log.
Once the printer clients have been set-up, they can have printer output sent through lp.
The installation of Fusion95 will automatically set-up eight lp printers named lprt00 through lprt07. These will direct spooled output via the smbprtup printer client program to their respective network printers.
Administration of UNIX print jobs are done using the standard UNIX "lp" administration tools.
It is very easy to expand the number of lp printers to the maximum of 1000 by adding Fusion95 printers into the lp subsystem. This is done using the normal UNIX system administrator menu.
Printing through lp can be tested using the following UNIX command:
ls -l | lp -d lprt03
If the output for some reason fails, a UNIX mail is sent to the user and depending on the level of the problem, the printer may become disabled.
Both named pipe printing and lp printing make use of the smbprtup utility. This utility can be executed directly from the command line or from any other script. The following example prints the ls -l output to the same printer as the examples above.
cd /usr/fusion95
ls -l | smbprtup -c./cfg/lprt03.cfg
Before the printer client can establish a session with the server, it must obtain the IP address of the server.
Most LANs, including Fusion95, implement the b-node method of locating servers as defined in RFC 1001/1002. This causes the client to send a broadcast name query request to attempt to locate the server name. A positive response includes the IP address of the server. This step will be bypassed if the printer is configured as not on the local LAN.
This method will not work if the UNIX printer client and the printer server are not on the same broadcast network, for example if they are connected via TCP/IP routers.
If the printer client fails to obtain the IP address of the printer server via a broadcast, the client will attempt to obtain the IP address using the UNIX gethostbyname function. This will search the local /etc/hosts file and any Domain Name Servers to resolve the address.
For example, to access a printer server called SERV95 on another network via a router add the following entry to the /etc/hosts file:
192.0.0.12 SERV95
Fusion95 provides a menu shell to allow the administrator to easily perform administration tasks.
The following command is used to execute the menu shell:
/usr/fusion95/fusion95
The menu shell is accessed and controlled through a series of window-like screens and menus. The following keys are used to move through the fusion95 screens:
| Key | Function |
|---|---|
| Up Arrow or Ctrl-K | Move up in a column |
| Down Arrow or Ctrl-J | Move down in a column |
| Right Arrow or Ctrl-H | Move to the right |
| Left Arrow or Ctrl-L | Move to the left |
| Enter or Return | Perform the operation that is currently highlighted |
| F5 | Execute a form |
| F9 or Ctrl-E | Exit the menu shell |
Menu items are provided to perform the following functions
Menu items are provided to perform the following functions
Menu items are provided to perform the following functions
Menu items are provided to perform the following functions
Menu items are provided to perform the following functions
Menu items are provided to perform the following functions
Menu items are provided to perform the following functions
This function checks the integrity of the installed Fusion95 files by calculating their checksum and matching with a list of expected checksums (held in checksum.txt).
A license utility is provided to maintain and update the Fusion95 license database.
The license utility can be executed using the command:
/usr/fusion95/license
It will display the following options:
Change License
Show License
Add License
In order to display all license codes in the Fusion95 license database, run the following command:
/usr/fusion95/license -s
This program can also be started by running the menu shell and selecting:
License Codes => Show License
This displays all the current licenses configured in the license database and a total of the number of authorized users.
line license code serial num users expiry date
----------------------------------------------------
1 FD1K-4M48-UNJ0-XRRT 1070043 2
2 Q2RR-4M48-YT7R-TYPO 1070192 10
3 P9P9-4RFV-UNJ0-MN6R 1070193 5
total authorized users = 17
In order to display add a license codes to the Fusion95 license database, run the following command:
/usr/fusion95/license -a
This program can also be started by running the menu shell and selecting:
License Codes => Add License
This option will allow you to add licensed users to your system. You will be prompted for the new license code. Enter the 16-character code in the following format:
XXXX-XXXX-XXXX-XXXX
In order to change or delete an existing license code from the Fusion95 license database, run the following command:
/usr/fusion95/license -c
This program can also be started by running the menu shell and selecting:
License Codes => Change License
The program will display the current licenses.
line license code serial num users expiry date
----------------------------------------------------
1 FD1K-4M48-UNJ0-XRRT 1070043 2
2 Q2RR-4M48-YT7R-TYPO 1070192 10
3 P9P9-4RFV-UNJ0-MN6R 1070193 5
total authorized users = 17
To change any license information, enter the line number to change and press return. You will be prompted to change the authorization code. Enter the 16-character code in the following format:
XXXX-XXXX-XXXX-XXXX
To delete the code, enter d.
An evaluation license can be used for a customer who wishes to test Fusion95 before purchasing a copy.
During the installation procedure of a new Fusion95 system the user will be asked if he has a license code. If he does not have a code, a 10 user evaluation license with a one month expiry date will be automatically generated.
When the license database is displayed, the expiry date will be shown along side this code.
line license code serial num users expiry date
----------------------------------------------------
1 D1K-4M48-UNJ0-XRRT Evaluation 10 29 Nov 1993
total authorized users = 10
The license scheme is accumulative. Thus if a user first installs a 10 user license, and at a later date installs a second 10 user license, the system will then support 20 users. It is not necessary to re-configure the kernel, re-boot the system, or even restart any part of Fusion95 in order to support these extra users.
The nbas utility is provided to obtain the adapter status of a NetBIOS node. This program has a command line of the following format:
nbas <options> <netbios name>
The -x option can be used to specify that the output will have the NetBIOS names displayed in hex, the default being ASCII.
Different options can be used to return information about different types of name.
nbas <Workstation name>
nbas -f <File server name>
nbas -d <Domain master browser name>
nbas -p <Primary domain controller name>
nbas -m <Master browser server name>
nbas -b <Browser server name>
The NetBIOS name should specify any name in the node from which adapter status is desired. Specifying no name or an "*" will display the adapter status of the local Fusion95 node.
An example of a nbas command is:
nbas KEITH
Which could produce the following output:
------ ADAPTER STATUS ------
Adapter Node Name/Address : 00 00 C0 C6 90 13
Free NCBs: 254 Maximum NCBs: 254
Active Sessions: 3 Maximum Sessions: 10
Packet Size: 1497
--- 6 NAMES in name table ---
1 "KEITH " 00 Redirector
2 "WORKGROUP " 00 Workgroup Group Name
3 "KEITH " 03 Messages
4 "KEITH " Server
5 "WORKGROUP " 1E Browser Server Group Name
6 "KEITH " 1F
Fusion95 can act as a server for just about any PC Client which uses the SMB protocol over an RFC TCP/IP NetBIOS.
The following is a list of some of the more common clients:
Before the client can establish a session with the server, it must obtain the IP address of the server.
Most PC networks, including Fusion95, implement the b-node method of locating servers as defined in RFC 1001/1002. This causes the client to send a broadcast name query request to attempt to locate the server name. A positive response informs the client of the IP address of the server.
This method will not work if the UNIX server and the client PC are not on the same broadcast network, for example if they are connected via TCP/IP routers.
Depending on the client software, there are different methods of locating the server without using broadcasts.
The LMHOSTS file contains a list of IP addresses and server names. On most versions of LMHOSTS, #PRE option should be used to pre-load the IP address. The pre-load option should always be used with Microsoft Windows to bypass a limitation in the LMHOSTS file scanning when DNS is enabled. On older versions this is treated as a comment and ignored.
The following is an example of an LMHOSTS file:
192.0.0.3 RS6000 #PRE
192.0.0.10 POWERPC #PRE
192.0.0.12 FUSION95 #PRE
The directory in which the LMHOSTS file should reside depends upon the client used. For example Windows for Workgroups and Windows95 use C:\WINDOWS and Windows NT uses C:\SYSTEM32\DRIVERS\ETC.
Centralized LMHOSTS
The #INCLUDE command can be used to include a centralized LMHOSTS file, so that all node names do not need to be distributed to all servers. Redundancy can be added using the commands: #BEGIN_ALTERNATE and #END_ALTERNATE. For example:
193.14.100.3 SERVER3 #PRE
192.14.101.10 HEADOFFICE #PRE
# BEGIN_ALTERNATE
#INCLUDE \\SERVER3\DISK\LMHOSTS
#INCLUDE \\HEADOFFICE\DISK\LMHOSTS
# END_ALTERNATE
Loading LMHOSTS
Early versions of RFC NetBIOS do not support the #PRE option to load names from the LMHOSTS file. Instead they provide the addname program in order to do this. This should be run after starting TCP/IP but prior to starting windows (e.g. in autoexec.bat). For example:
addname /load
Run the addname command without any options to show which NetBIOS names have been loaded.
This is known to be required on LAN Manager. This is even required on Windows for Workgroups with the old 16 bit TCP/IP stack, but not with the current TCP/IP-32 stack.
With Pathworks
DEC Pathworks uses the same method as described above, but the program and file names have however been changed. The "LMHOSTS" file is called C:\PW\NBHOSTS, and the "addname" program is called inetname.
Some clients, including Windows95 and Windows/NT can obtain the IP address of a server from a Domain Name Server (DNS). This does however require that the Fusion95 node name is the same as the host name of the UNIX machine.
Some clients, including Windows95 and Windows/NT can obtain the IP address of a server from a Windows Name Server (WINS). Although the released Windows for Workgroups 3.11 cannot use a WINS, an updated VREDIR.386 is freely available to enable it to do this. This VREDIR.386 is even distributed on the Windows/NT release CD-ROM.
The NBTSTAT utility can be used at the Windows95 MS-DOS Prompt to determine if the Fusion95 server can been "seen". Run the command twice, first using the Fusion95 server’s IP address and then using it’s network name.
NBTSTAT -A 197.12.112.101
NBTSTAT -a FUSION95
If the NetBIOS name to IP-address resolution is working correctly, both of these commands will return the status from Fusion95.
The Fusion95 server sends out browse datagrams to announce its presence on the network. These "Host Announcement" datagrams are gathered up by a browse master. Workstations the ask the browse master for the list of available servers.
For browsing to function correctly, one or more Browse Masters must be configured on the network. A Windows for Workgroups or Windows95 machine can be enabled as a browse master. A Windows NT machine is a browse master by default.
To make Windows for Workgroups run as a Browse Master it is only necessary to enable disk and printer resource sharing. This will automatically enable the Browse Master.
In order to configure Windows95 to run as a Browse Master, perform the following steps:
From the "Control Panel", start the "Networks" configuration program.
Make sure that "File and Printer Sharing for Microsoft Networks" is enabled.
Select "File and Printer Sharing for Microsoft Networks" and click the "Properties" button.
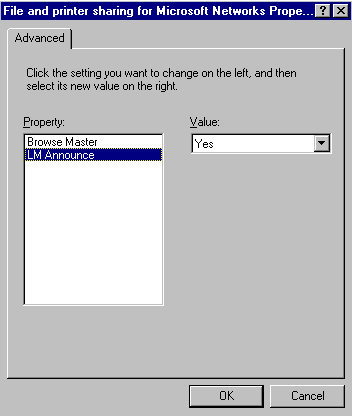
Make sure that the Browse Master property has a Value of Automatic or Enabled.
This section explains how to use the Fusion95 server from a PC workstation running DOS, or from the DOS prompt in a Windows or OS/2 workstation.
It is possible to use disks manually via the NET USE command, automatically when a PC workstation is started or when the user logs on, or via a number of different client specific Windows interfaces. For further details of how to do this consult the operating system documentation.
An example command to use a Fusion95 disk resource called ACCOUNTS on the server called FUSION as the PC’s disk F: would appear as follows:
NET USE F: \\FUSION\ACCOUNTS
If the disk resource was password protected, the password should be appended to the command line:
NET USE F: \\FUSION\ACCOUNTS SECRET
When it is no longer required to use the disk, the /D option removes it from the PC’s use list.
NET USE F: /D
It is possible to use printers manually via the NET USE command or automatically when a PC workstation is started.
An example command to use a Fusion95 printer resource called HPLASER on the server called FUSION as the PC's printer LPT2: would appear as follows:
NET USE LPT2: \\FUSION\HPLASER
If the printer resource was password protected, the password should be appended to the command line:
NET USE LPT2: \\FUSION\HPLASER SECRET
When it is no longer required to use the printer, the /D option removes it from the PC’s use list.
NET USE LPT2: /D
To test that the NET USE worked correctly, try the following command:
COPY C:\AUTOEXEC.BAT LPT2:
This section explains how to use the Fusion95 server from a PC workstation running
Windows for Workgroups.
In order to used a shared disk resource, run the File Manager program. From the "Disks" menu select "Network Connections...". You will be prompted with the following:
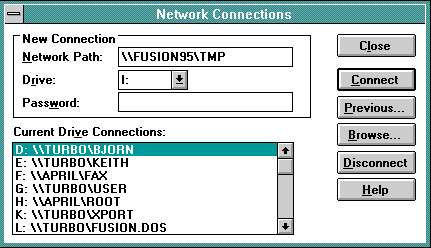
In the Network Path box, type two back-slashes followed by the name of the Fusion95 server, another back-slash and then the name of the shared disk (e.g. \\FUSION95\TMP). Optionally change the drive letter, and type the password. Finally select "Connect".
In order to used a shared printer resource from Windows, run the Print Manager program. From the "Printer" menu select "Network Connections...". You will be prompted with the following dialog box:
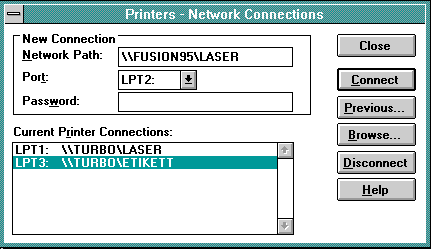
In the Network Path box, type two back-slashes followed by the name of the Fusion95 server, another back-slash and then the name of the shared printer (e.g. \\FUSION95\LASER). Optionally change the printer port, and type the password. Finally select "Connect".
This section explains how to use the Fusion95 server from a PC workstation running Windows 95, 98 or NT 4.
In order to used a shared disk resource, run the Windows Explorer program. From the "Tools" menu select "Map Network Drive...". You will be prompted with the following dialog box:
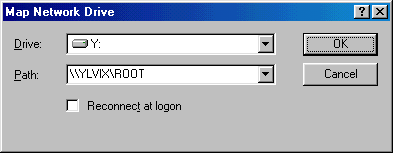
In the Path box, type two back-slashes followed by the name of the Fusion95 server, another back-slash and then the name of the shared disk (e.g. \\FUSION95\TMP). The first free drive will be shown, change this if required. Select "OK"; you will be prompted for a password if one is required.
Alternatively you can use the Network Neighborhood icon in the Windows Explorer program to browse the network to find the server and resource you wish to connect.
Click Network Neighborhood to show all servers in your workgroup or domain. Click on the server to obtain a list of the resources it shares. Click on the resource using the RIGHT mouse button to obtain a pop-up menu.
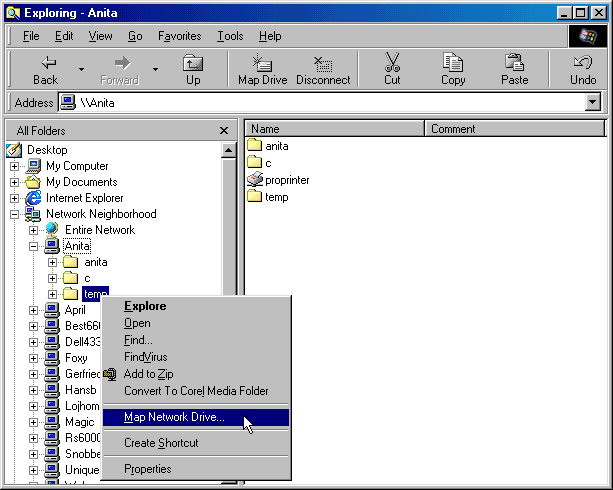
Select "Map Network Drive…" from the pop-up menu. The first free drive will be shown, change this if required. Select "OK"; you will be prompted for a password if one is required.
In order to used a shared printer resource, select Settings and Printers from the Start menu and run the Add Printer icon.
Choose the "Network printer" option.
In the "Network Path or Queue Name" box, type two back-slashes followed by the name of the Fusion95 server, another back-slash and then the name of the shared printer (e.g. \\FUSION95\MATRIX). If you are unsure of the server or printer name, you can use the browse button to locate it.
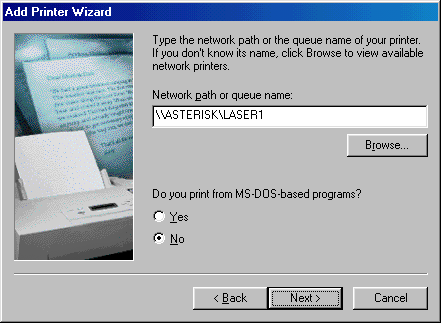
You must install, or already have installed, the correct Windows printer drivers for the type of printer being installed.
This chapter describes how to use Passthrough Authentication in Fusion95. This feature can be used on all platforms. It explains how to use Passthrough Authentication to verify user credentials (user/password) using an Windows NT or 2000/XP Domain Controller.
Passthrough Authentication is a mechanism used by a Common Internet File System (CIFS) server to validate user credentials (user/password) with an Windows NT or 2000/XP Domain Controller and thus grant the user access to a resource on the server, following a successful validation of the user credentials by the Domain Controller
The following requirements must be met in order to use Passthrough Authentication in Fusion95.
After a new installation you can find information about the new passthrough_server keyword in the pcserve.ini in the /usr/fusion95/cfg directory. If you have performed an upgrade, you can find the information in the inifile.txt file in the same directory.
If Fusion95 is running, then stop it . Run: /usr/fusion95/f95stop
Add a passthrough_server=<server-specification> entry in the pcserve.ini file located in the /usr/fusion95/cfg directory. The <server-specification> is explained below in Passthrough Server Specification.
To start Fusion95, run: /usr/fusion95/f95start
The Passthrough Server variable in the pcserve.ini file is used to specify the Domain Controller you wish to use for validation of user credentials (user/password).
Domain Controller and Unix machine on the same broadcast network
Typically you would specify: DomainName\ServerName. The ServerName must be specified as a Network Node Name.
Example: passthrough_server=DOMAIN2\SERVER7
Domain Controller and Unix machine on different broadcast networks
If Fusion95 and the Domain Controller reside on different broadcast networks then you must specify: \ServerName. The ServerName can be specified as either a Network Node Name or as an ip-address in dot notation (a.b.c.d). If you specified a Network Node Name, then the name must be able to be resolved by an entry in the /etc/hosts file, or by a Domain Name Server (DNS).
Examples: passthrough_server=\RSERVER or passthrough_server=\101.102.103.104
Redundancy
More than one server can be specified to allow for redundancy. Separate the entries with a semicolon.
Example: passthrough_server=DOMAIN2\SRVR2;DOMAIN2\SRVR4
You activate the Default User feature by adding a user named "__DEFAULT__" (two underscores before and after DEFAULT) into the Fusion95 database. As result a user that does not exist in the Fusion95 database will adopt the properties you specified for the Default User. Thereafter, the normal Passthrough Authentication procedure will take place, of course using the original user name.
By using the Default User feature you do not need to add all users in the Windows network into the Fusion95 user database. You only need to add those users that you wish to assign special properities, for example users you want to assign the Fusion server administrative rights.
To deactive the Default User feature, you simply remove the "__DEFAULT__" name from the Fusion95 database.
For information on how to add a user into, or
remove a user from the Fusion95 database, refer to the Fusion95 User's Guide.
You will probably want to limit the capabilities of the Default User.
For example not map to the root unix user.
There is no need to reboot the server to activate or deactive this feature, you just add or remove the "__DEFAULT__" name.
The authentication with the passthrough server is performed using the origiinal user name. This feature is only available with User Level Security (not with Unix Level Security).
This chapter explains how to enhance your Fusion95 server to make it a Network Log On server.
A Windows client PC running Windows for Workgroups or Windows95 can log on to the Fusion95 machine and execute a log on script. This log on script is used to automate various tasks such as the NET USE of disk resources or the updating of software.
The current version cannot function as a Domain Controller, so cannot be used to log on Windows NT workstations or servers.
The Fusion95 server can act as a Log On server for all workstations in a single domain. All workstations and servers in this domain must have the same domain name. The domain name may not be the same name as already possessed by a workstation in the network.
Windows NT and LAN Manager use the term domain, while Windows95 and Windows for Workgroups use the term workgroup to describe a logical group of computers. Throughout this manual we use the term "domain" to mean "workgroup or domain".
The following requirements must be met to use Fusion95 as a Network Log On Server for a Windows PC.
The following describes how to enable the log on server on a Fusion95 machine.
This should NOT find a NetBIOS node with the workgroup/domain name specified, but should return an time-out error 5.
The following describes how to disable the log on server on a Fusion95 machine.
A directory must be created on the Fusion95 server to contain the users’ logon scripts. We suggest using the name /usr/fusion95/netlogon.
mkdir /usr/fusion95/netlogon
Make sure that this directory has the correct user access permissions. This can be done as follows.
chmod 0755 /usr/fusion95/netlogon
In order to use the Fusion95 server as a Network Log On Server a shared disk called NETLOGON must be created. See the Sharing a Disk resource section in the File and Print Server chapter. See the Security Modes section in the File and Printer Server chapter See the Security Modes section in the File and Printer Server chapter
To add a NETLOGON resource carry out the following steps.
For each user that will log on, create a log on script in the directory pointed to by the NETLOGON shared resource. The log on script should have the same name as the user with the extension .BAT. If no script is present the user can still log on, but no automatic script execution will be performed.
The user ANITA should have a log on script with the name ANITA.BAT. It could contain the following commands to connect Anita’s 7 disk resources:
NET USE D: \\FUSION\BJORN /YES
NET USE E: \\FUSION\KEITH /YES
NET USE F: \\SERVER\FAX /YES
NET USE M: \\SERVER\MAIL /YES
NET USE R: \\DEVELOPMENT\ROOT /YES
NET USE W: \\WEBSERVER\HTML /YES
NET USE X: \\SERVER\BIN /YES
Fusion95 can act as a log on server for Windows for Workgroups, Windows 95 and Windows 98 PC Clients.
All PC clients wishing to log on via Fusion95 must have the same domain name as the Fusion95 server.
These clients must be configured to validate their log on via a log on server rather than via the local password file.
In order to configure Windows for Workgroups to use a log on server, perform the following procedure.
From the program manager select the control panel. In the control panel select the network icon.
Make sure that the workgroup name is set to the same as that configured in the Fusion95 server.
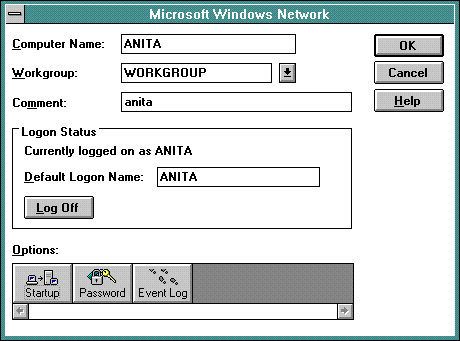
Select the startup settings. Make sure that the "Log On to Windows NT or LAN Manager Domain" is selected and that the Domain Name is the same as that configured in the Fusion95 server.
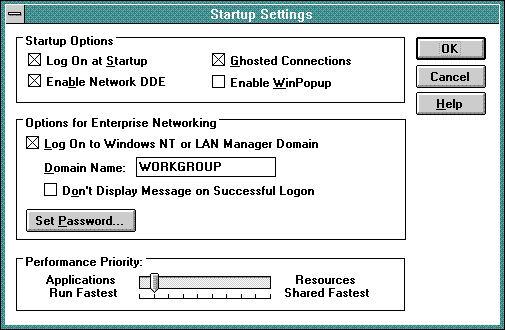
Once log on is enabled, the workstation must be restarted for the changes to take effect.
The user will be automatically prompted for user name and password when the PC starts.
If it is desired to log off and/or log on again as a different user without restarting the PC, the Log On/Off icon in the Program Manager’s Network group can be used.
In order to configure Windows95 and Windows98 to use a log on server, perform the following procedure.
From the start menu, select setting and control panel. In the control panel select the network icon. Select Client for Microsoft Networking, and click the properties button.
Make sure that the Log on to Windows NT domain is selected and that the Windows NT domain has the same name as that configured in the Fusion95 server.
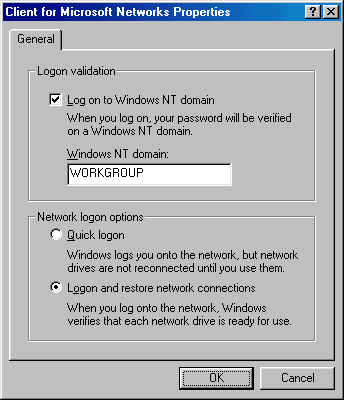
Once log on is enabled, the workstation must be restarted for the changes to take effect.
The user will be automatically prompted for user name and password when the PC starts.
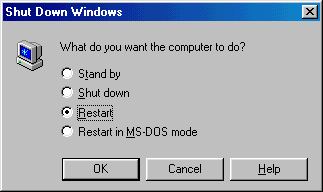
If it is desired to log off and/or log on again as a different user without restarting the PC, select Shutdown from the start menu.
Select Close all programs all log on as a different user.
If the homeshare option has been enabled in the /usr/fusion95/pcserve.ini pcserve.ini file then Fusion95 will report your home directory to the client and the /HOME option can be used in conjunction with NET USE.
The /HOME option makes a connection to your HOME directory if one is specified for your user account. For example:
NET USE H: /HOME
This appendix lists some of the common problems user’s have had with Fusion95 and the solution to them.
Check that Fusion95 is running correctly with the command:
# cd /usr/fusion95
# ./f95check
Check the contents of the /usr/fusion95/*0.log files. They may contain useful information for problem resolution.
With Fusion95 stopped, perform the steps described in Chapter 2 under TCP/IP Verification.
Check that you do not already have a RFC NetBIOS installed. The will cause pcserve to log the error "bind failed: Address already in use" in the pcserve0.log file Make sure that Fusion95 is stopped, and run the command:
# netstat -na | grep 13[789]
This should not show any users of sockets 137, 138 or 139 which are required by Fusion95.
Check that the workgroup/domain name is the same on all nodes.
Check that your are on the same physical network.
Check that you have correctly configured the network mask in the UNIX machine.
Check that you have a browse master in the network. A windows PC can be made into a browse master by making it into a server.
Check that a workstation can map a network drive on the Fusion95 server by specifying a hard path (e.g. \\FUSION\TEMP) instead of browsing.
Run the following UNIX command to obtain trace information (change the workgroup name as appropriate) The trace.txt file may contain useful information for problem resolution:
# cd /usr/fusion95
# ./wbeacon -dWORKGROUP -tnC1 2>&1 | tee trace.txt
If problems occur when the printer client attempts to access a user-level (e.g. NT) server.
The smbprtup program uses Core-Level SMB protocol, which is designed to access Share-Level servers. Accessing User-Level servers such as Windows NT (or maybe Windows95 depending upon configuration) from Fusion requires special configuration.
The following considerations apply:
If a PC program incorrectly complains about disk space full on the Fusion95 server.
Check that the Fusion95 server does not have disk partitions greater the 2GB. Some PC programs cannot handle such large disk sizes. Change the /usr/fusion95/cfg/pcserve.ini to include the line:
maxdisksize=1048576
This informs the server to never return disk information larger than 1GB (i.e. 1048576 KB). If a disk has more than 1 GB free only 1 GB will be returned. Once the free space drops below 1 GB, the true free space will be returned.
Check that the Fusion95 node name does not have a wrong entry in the workstations LMHOSTS file.
Add the Fusion95 node name and IP address to the workstations LMHOSTS file. This should not normally be required but is a good diagnostic step. Windows provides a sample LMHOSTS file called LMHOSTS.SAM.
The entry should have the format:
193.14.171.12 FUSION #PRE
Restart the PC to make Windows load the new LMHOSTS file.
Make sure that Fusion95 is stopped. Run the following UNIX command to obtain trace information:
# cd /usr/fusion95
# ./nbns -n15 2>&1 | tee nbns0.txt
Hit ctrl-c to abort the program. The trace.txt file may contain useful information for problem resolution. Check that the IP address of the Fusion95 node is shown correctly.
This appendix lists some of the platform specific problems user’s have had with Fusion95 and the solution to them.
If Fusion95 performs slowly when running on a Motorola 88K System V Release 3.2 system check the OSTYLE parameter.
Run the sysgen utility to configure the kernel. Check that the value of OSTYLE in the NSE tunable parameters is set to 1.
If this parameter needs to be changed, the kernel must be rebuilt.
When using DG UNIX on an Intel based platform, you must first install the DGUX.ACO library. If this is not done, it will not be possible to execute the Fusion95 programs.
Triggers are a feature of the File and Print server that allow the administrator to configure certain actions to be carried out when a certain event occurs.
An example of a trigger would be every time a user logs on to Fusion95 to execute a program passing the name of the user as a parameter.
Different trigger commands can be configured for each event. Trigger commands will be read in each time a workstation connects or reconnect and not just start-up.
Trigger commands can contain parameters (of the format !x) which will be automatically replaced in trigger command at execution time.
The trigger command’s return code can be used to cause the server to return an error to the client.
Individual shared resources can be configured to specifically exclude triggers support.
To enable triggers the pcserve.ini file must contain a triggers= parameter. This is set to 1 to enable triggers or 2 to enable triggers with trace output.
A value of 0 or no entry will disable triggers.
A text file called /usr/fusion95/cfg/triggers.ini must be created to configure triggers.
This file will contain the trigger command an if required a list of shared resources to support triggers.
Each required event should be placed in the [triggers] section of the triggers.ini file followed by the command to execute when that action is triggered.
Valid events and their action numbers are…
0 CONNECT
1 DISCONNECT
2 LOGON
3 LOGOFF
4 DISKUSE
5 DISKUNUSE
6 PRINTUSE
7 PRINTUNUSE
8 OPEN (of an existing file)
9 MOVE
10 UNLINK (and probably delete)
11 IPCUSE
12 IPCUNUSE
13 CREATE (and open of a new file)
Each event in the configured in the triggers.ini file should be followed by the command to execute when that event occurs.
The trigger command line is parsed and all known !x parameters are replaced. Then the command line is executed. Note: you can have extra text (e.g. options) on the command line and that even the program name can include a !x.
Example: if you write one program per action, and call the program the same as the action, then the following trigger could be used...
open=/usr/trig/!a !w !u !s !f !d !m
Example: if you wanted to pass the mode number as a -m option then you can write the following...
open=/usr/trig/!a !w !u !s !f !d -m !m
Valid parameters for a trigger command are listed below:
!a action/event name
!A action/event number
!w workstation name
!s share name
!n filename; no path
!f filename; path from root
!d directory; path from root
!F filename; path from share
!D directory; path from share
!m file open mode; decimal
!M file open mode; text
The following command parameters are only supported when the server is running in User-Level or Unix-Level security mode:
!u PC user name
!U UNIX user name
!i UNIX UID
!I UNIX GID
The !M file open mode parameter returns the following:
RO Opened for reading
WO Opened for writing
RW Opened for reading and writing
EXEC Opened to executed the file
Not all events support all parameters. The following is a list of which parameters support which actions.
| Event | Supported parameters |
|---|---|
| CONNECT | !a !A !w |
| LOGON | !a !A !w !u |
| DISCONNECT, LOGOFF |
!a !A !w !u !U !i !I |
| DISKUSE, DISKUNUSE, PRINTUSE, PRINTUNUSE, IPCUSE, IPCUNUSE |
!a !A !w !u !U !i !I !s |
| MOVE, UNLINK |
!a !A !w !u !U !i !I !s !n !f !F !d !D |
| OPEN, CREATE |
!a !A !w !u !U !i !I !s !n !f !F !d !D !m !M |
The return code from the trigger command can be used to cause the server to return an error to the client.
The command for the Connect event should return 0 to permit the connect and non-zero to refuse the connect.
The return code from the command for the Disconnect event is ignored.
Commands for other events should:
Common return codes that might be used are:
2. File not found.
3. Directory invalid.
5. Access denied.
32. Open mode conflicts with existing open.
67. No such disk name in net use (from NT)
102. Invalid password supplied on net use.
104 . Access denied. (usually on net use from NT)
106. No such disk name in net use.
The [disks] section of the triggers.ini file is used to disable triggers on each disk.
To disable triggers on a specific disk name set it to a null value (e.g. disk1=).
To disable triggers on all but a certain tree within a disk set the disk name to the value of the root of the tree within the disk (e.g. disk2=/tmp). The default which enable triggers on the whole disk is a value of / (e.g. disk3=/ is the same as no disk3 entry).
The following is an example of a trigger configuration file (/usr/fusion95/cfg/triggers.ini). It executes a shell script when a trace event occurs:
[triggers] connect=/bin/sh trig !a !w disconnect=/bin/sh trig !a !w !u diskuse=/bin/sh trig !a !w !u !s diskunuse=/bin/sh trig !a !w !u !s open=/bin/sh trig !a !w !u !s !F !f !m unlink=/bin/sh trig !a !w !u !s !F !f move=/bin/sh trig !a !w !u !s !F !f [disks] programs= appl1=/ appl2=/data